Australia is witnessing a meteoric rise in cybercrime, a trend that not only echoes globally but also rings an alarm for immediate action. With a cyber attack occurring every six minutes, Australian businesses and individuals find themselves in the crosshairs of an invisible war, one waged in the realm of zeros and ones.
The Surge in Cybercrime: A Statistical Glimpse
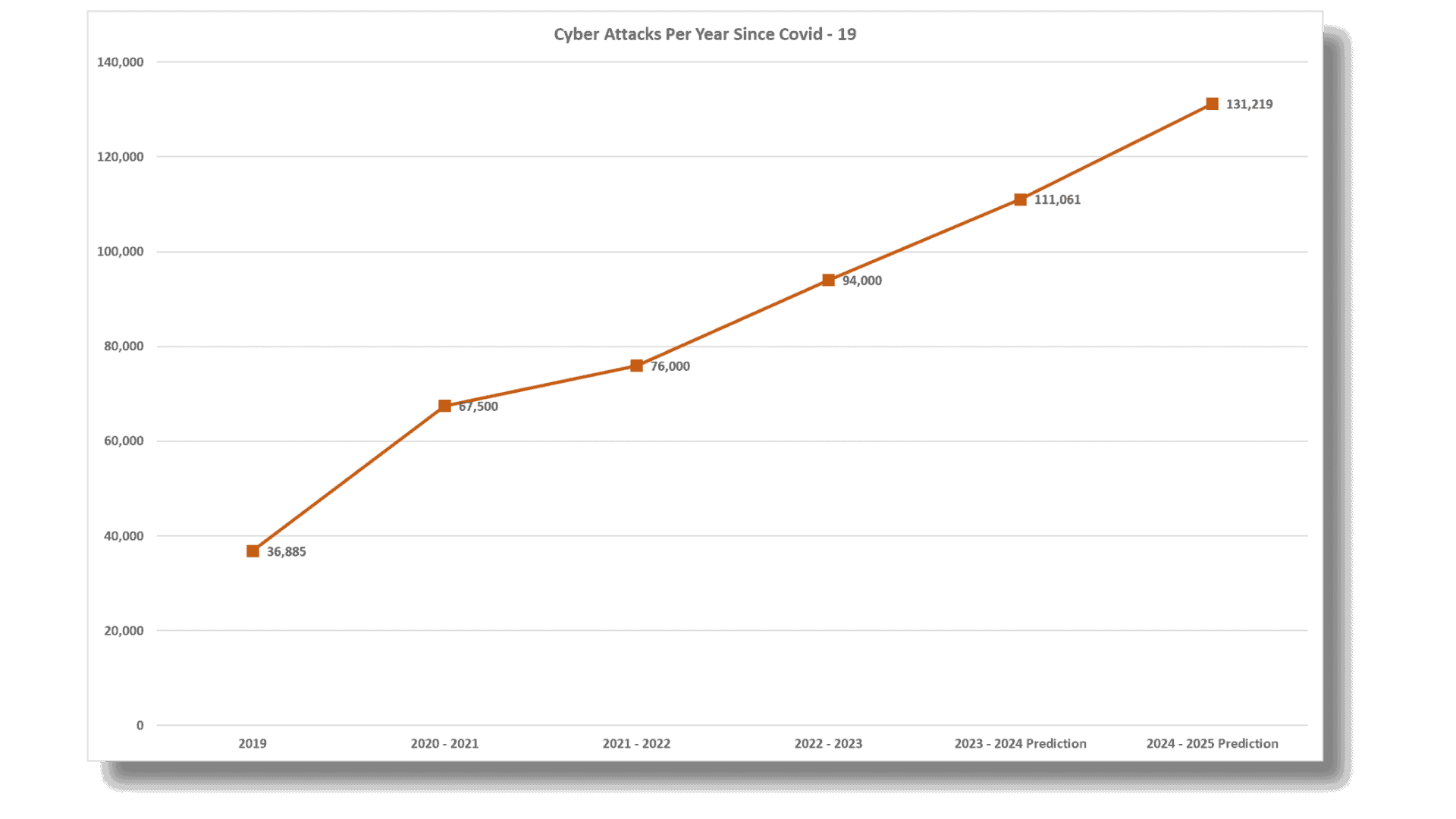
Since the Covid-19 pandemic hit, Australia has seen a dramatic increase in cybercrimes, and it doesn’t look like it is going to slow down
2020-2021: During this time, we started seeing more cybercrimes. There were over 67,500 reports, which was a lot more than the year before. It was a clear sign that these online crimes were becoming a bigger problem.
2021-2022: Things got even busier on the cybercrime front. There were about 76,000 reports, which means it went up by 13% from the year before. To give you an idea, that’s like having a cybercrime happen every seven minutes.
2022-2023: This is where it gets even more serious. The reports shot up to around 94,000, roughly one cyber attack every six minutes. This big jump shows us that cyber attacks are happening more often and are a growing issue we need to deal with.
Compromised Emails: The Business Battlefield
Australian businesses battle for security and trust, compromised emails have emerged as a primary weapon wielded by cybercriminals. These deceptively simple attacks pack a powerful punch, striking at the heart of a company’s operations and integrity.
The Deceptive Nature of Email Compromise: These attacks often masquerade as legitimate communications, making them particularly dangerous. They might look like routine requests from suppliers or even internal directives from senior management. The attacker’s goal is to trick an employee into taking an action that opens the door for further exploitation – be it transferring funds, divulging sensitive information, or granting access to critical systems.
Financial Fallout: The direct financial impact of these breaches can be staggering. From funds being misdirected to fraudsters, to the cost of investigating the breach and strengthening security post-incident, the financial drain is immediate and substantial. For small and medium-sized enterprises, such an event can be particularly crippling, sometimes sapping resources that were earmarked for essential business growth.
Erosion of Trust and Reputation: Perhaps even more damaging in the long term is the erosion of trust – both from customers and within the organization. When customers learn that a business has fallen victim to such an attack, their confidence can waver, leading to a loss of business. Internally, employees may question the robustness of their systems and their ability to safeguard sensitive information, which can impact morale and productivity.
The Challenge of Restoration: Restoring customer trust and rebuilding a tarnished reputation is often a more complex and prolonged process than addressing the immediate financial losses. It involves not only reinforcing cybersecurity measures but also engaging in transparent communication with stakeholders and often a prolonged period of rebuilding customer relationships.
The Financial Fallout
Every cyber attack not only jeopardizes data but also inflicts a severe financial blow. For Australian businesses, the cost of falling victim to cybercrime can be devastating. Small businesses, which form the backbone of the economy, face an average loss of $46,000 per incident. For medium-sized businesses, the damage is even more staggering, with costs soaring to about $97,200. And large corporations are not spared, facing an average impact of $71,600 per cybercrime event.
But the financial implications are just the tip of the iceberg. Here’s a sobering fact: 60% of small and medium-sized businesses (SMBs) that suffer a cyber attack go out of business within six months of the incident. This statistic isn’t just a warning; it’s a stark reminder of the existential threat posed by cybercrimes. The financial strain can cripple operations, erode customer trust, and ultimately lead to the downfall of a business.
These figures are not mere numbers; they represent the real and often overwhelming challenges that businesses face in the wake of a cyber attack. From the local shops to the sprawling corporate networks, the financial tornado of cybercrime can upend businesses, underscoring the critical need for robust cybersecurity measures across the board.
Beyond Borders: The International Intrigue
The battlefield of cybercrime in Australia isn’t just local; it extends far beyond its shores, entangled in a complex web of international intrigue. The Australian Signals Directorate (ASD) has cast a spotlight on the sophisticated nature of these global threats, particularly highlighting entities from China as notable aggressors in the cyber arena.
International Espionage and Data Theft: These international cyber adversaries are not amateur hackers; they are often part of well-organized, state-sponsored groups with specific agendas. Their targets? Australia’s lucrative and sensitive business data. From trade secrets to cutting-edge research, these digital assailants are on a quest to siphon off valuable information that can bolster their own economic or strategic positions.
The Challenge of Attribution and Defence: One of the most daunting aspects of these international cyber threats is their nebulous nature. Pinpointing the exact origins of an attack, given the sophistication and the use of advanced obfuscation techniques by these actors, is a formidable challenge. This ambiguity not only complicates the process of holding these entities accountable but also makes it more challenging for businesses and government agencies to anticipate and defend against such attacks.
Broader Implications for Australian Commerce: The global dimension of these cyber threats adds a layer of complexity to Australia’s threat landscape. Cyber attacks can be launched from any corner of the globe, exploiting the interconnected nature of modern commerce and technology. This reality requires Australian businesses and policymakers to not only fortify their digital defences but also engage in international cooperation to combat these threats effectively.
Need for a Collaborative Global Response: Addressing these threats transcends individual organizational capabilities and calls for a coordinated international response. Sharing intelligence, aligning on cybersecurity standards, and collaborative law enforcement efforts are crucial steps in building a resilient global framework against such sophisticated cyber threats.
The Human Element: Our Achilles Heel
The Australian Cyber Security Centre’s report underscores the critical role of human error or oversight in cybersecurity breaches. These vulnerabilities often stem from everyday actions within an organisation, such as employees inadvertently opening suspicious emails or mishandling digital requests and credentials.
This emphasis by the ACSC on human factors sheds light on an essential aspect of cybersecurity: technology alone isn’t enough to safeguard against cyber threats. There’s a pressing need for a cultural shift within organisations, where cybersecurity awareness and good practices are embedded in the fabric of daily operations.

Enhancing cybersecurity involves regular and engaging training for staff, consistent enforcement of policies, and creating an environment that encourages vigilance and proactive reporting of potential threats. This focus on the human element highlights that effective cybersecurity is not just about deploying advanced systems, but also about empowering the people who use them with the knowledge and tools to identify and mitigate risks.
By prioritising human aspects in cybersecurity strategies, organisations can significantly reduce the likelihood of breaches and build a more resilient defence against cyber threats.
Building a Cyber-Resilient Australia
Awareness is the first step towards building a cyber-resilient Australia. Businesses must not only acknowledge the severity of the threat but also take proactive steps to mitigate it. This involves a multi-faceted approach encompassing education, infrastructure, culture, and expert collaboration.
1. Cultivating Cyber Literacy
Educating staff on the hallmarks of cyber scams is crucial. Regular training sessions, simulated phishing exercises, and clear communication channels for reporting suspicious activities can significantly bolster a company’s defences. It’s about creating a workforce that is not just aware but also proactive in identifying and mitigating cyber threats.
2. Investing in Robust Cybersecurity Infrastructure
Investing in cybersecurity is investing in the business’s future. State-of-the-art security systems, multi-factor authentication, and regular software updates are not just tools but necessary shields in the digital arena. These measures, while requiring initial investment, pay off by safeguarding valuable data and maintaining business continuity.
3. Embracing a Culture of Vigilance
Creating a workplace culture where cybersecurity is everyone’s responsibility is vital. It’s about fostering an environment where vigilance is a reflex, not an afterthought. This cultural shift ensures that cybersecurity is integrated into every business process and decision, making it a cornerstone of the organisational ethos.
4. Engaging with Experts: The Role of Surety IT
For businesses grappling with the complexities of cybersecurity, engaging with experts like Surety IT can be a game-changer. Surety IT provides tailored solutions that fit the unique needs of each business. From assessing vulnerabilities to implementing cutting-edge security measures, they offer a comprehensive approach to cybersecurity. Their expertise in understanding the Australian cyber landscape makes them a crucial ally for businesses looking to strengthen their cyber defences.
5. Government and Private Sector Collaboration
A united front between the government and the private sector is imperative. Sharing intelligence, best practices, and resources can amplify the collective defence against cyber threats. This collaboration paves the way for a more resilient digital ecosystem, where businesses can thrive with confidence.
Confronting Cyber Threats: The Imperative for Action in Australia’s Cybersecurity Landscape
The Australian Signals Directorate’s recent report throws a spotlight on the increasingly complex and challenging cybersecurity landscape in Australia. It’s a landscape where threats evolve rapidly, and the stakes are continuously rising. For Australian businesses and individuals alike, this situation demands more than just awareness; it calls for proactive and comprehensive action.
As cyber threats become more sophisticated, the need for robust cybersecurity strategies becomes paramount. It’s no longer sufficient to react to incidents as they occur. Instead, a forward-thinking approach, one that anticipates potential threats and builds resilient systems to counter them, is crucial.
This proactive stance involves deploying advanced security measures, conducting regular risk assessments, and ensuring continuous monitoring and updating of security protocols. However, as the ASD report points out, technology is only part of the solution. Equally important is the cultivation of a cybersecurity-conscious culture within organisations – where every employee is aware of potential threats and how to avoid them.
Take Action with Surety IT: Your Partner in Cybersecurity
In facing these challenges, partnering with a seasoned cybersecurity expert like Surety IT can make a significant difference. Surety IT offers tailored solutions to fortify your digital defences, ensuring that your business is not only protected against current threats but is also prepared for future challenges.
Whether you’re a small business grappling with the nuances of cybersecurity or a large corporation seeking to enhance your existing security measures, Surety IT has the expertise and solutions to meet your specific needs. From vulnerability assessments to implementing advanced cybersecurity technologies and training your team, Surety IT is your dedicated partner in navigating the complex cybersecurity landscape.
Don’t wait for a breach to occur. Take action now. Contact Surety IT to protect your business and secure your peace of mind in the digital age. Together, we can build a safer and more resilient digital future for your business.
Useful Links
The Ultimate Guide To Cybersecurity For Modern Businesses
12 Questions Business Owners Might Be Afraid To Ask About Cyber Security
Strengthen Your Business’s Defence With Cyber Shield Vanguard And Cyber Shield Elite





