Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include;
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
PayPal Phishing Email
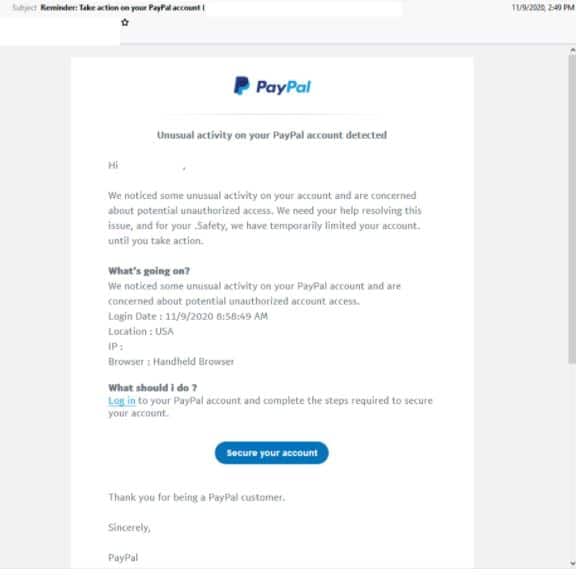
- Impersonates global online payments system PayPal. The subject reads: ”Reminder: Take action on your PayPal account”
- The email body employs the PayPal logo. However, the email address uses a domain not belonging to PayPal highlighting it’s illegitimacy.
- Email begins with the header ‘unusual activity on your PayPal account detected’. It informs recipients that their accounts have been “temporarily limited” for their safety until they complete the steps to secure their account.
- Clicking the link to login in to secure the account leads to a phishing page whereby they are requested to login to their PayPal account.
- Once the user enters their information they are lead to several more phishing pages requesting they submit their personal information like:
– Credit card details
– Banking details
– Documents to verify identity like passport and driver’s license
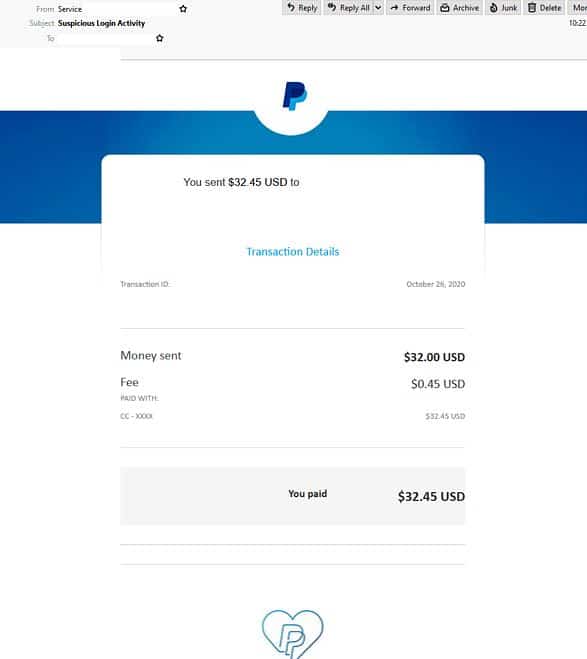
- Another email impersonating PayPal to look out for is titled “Suspicious Login Activity” and uses the display name ‘service’.
- It employs PayPal’s branding and logos yet the domain used does not belong to the company.
- The body of the email is designed to appear as a transaction alert. It claims if users don’t recognise the transaction they can claim a refund and informs them of the temporary suspension of their account until their identity can be confirmed.
- Recipients who click the link are led to a fake PayPal login page. Once logged in they are redirected to a page informing them “access to sensitive account features will be limited” and are provided with a button to continue.
- Users who click continue are led to similar pages requesting personal information like credit card details.
- Finally after entering these details, users are shown a ‘Thank you’ page before being redirected to the real PayPal website.
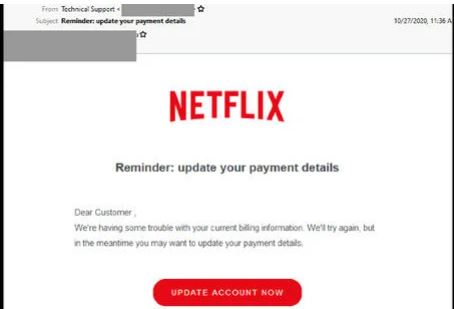
Netflix Phishing email
- Purports to be from popular entertainment company Netflix. The subject reads: “Reminder: update your payment details”
- Claims to be a notification from the technical support team and employs the Netflix logo and branding. However the email address uses a domain not belonging to Netflix.
- Informs users of issues with their current billing information and requests they update their billing information.
- Clicking the link to update the account redirects users to a compromised WordPress site designed to harvest the users’ Netflix account and credit card information.
Machinery Trader Phishing Email
- Impersonates construction equipment advertising website, Machinery Trader. The subject reads: “You have (1) new inquiry message”
- The email body includes the company logo and branding but is actually from a compromised account.
- It informs recipients of an inquiry message about their ad and instructs they login to their account to view the message.
- Clicking the link to login to their account users are lead to a fake Machinery Trader login page employing the website’s logo. But instead of replicating the style of the real log in page, the majority of the phishing page’s background is an image, alerting to its illegitimacy.
- Once the users log in to their account they receive an error message saying the password they entered is invalid.

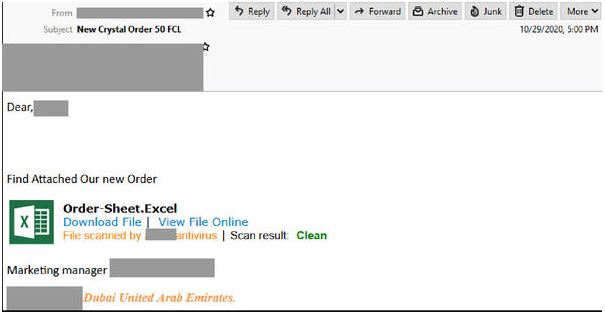
Compromised SendGrid Account
- This email purports to be form a marketing manager but is actually Sent from a compromised SendGrid account.
- Titled “new Crystal order 50 FCL” it informs recipients new order is attached.
- The body of the email contains a link that appears to be a Microsoft Excel file scanned by an anti-virus service.
- Clicking the link leads recipients to a Google Drive branded page. However, the domain used does not belong to Google or Microsoft.
- The page includes images and links of various files in different formats.
- Once a user clicks one of these files they are led to a login page and asked to submit their credentials.
- Then they are met with an error message saying the password they entered is invalid.
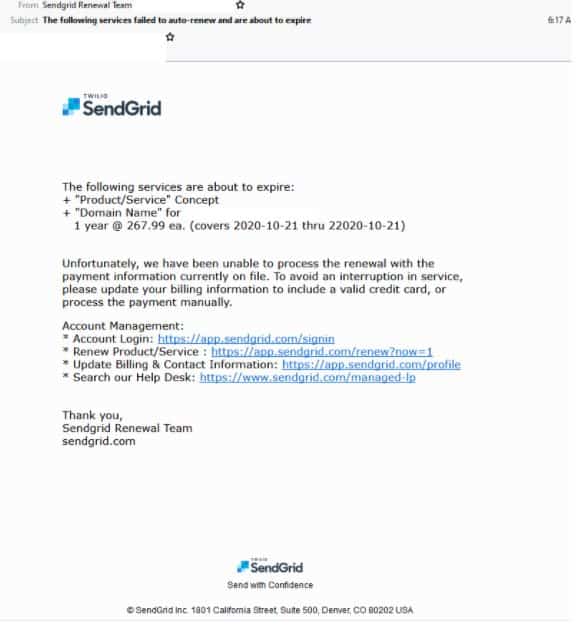
- Another phishing email claiming to be from SendGrid is titled “The following services failed to auto-renew and are about to expire” and uses the display name ‘Sendgrid renewal team’ the inaccurate spelling of the display name highlights this email’s illegitimacy.
- The body of the email employs SendGrid’s branding and logos and fake support links to try and boost it’s credibility. However this email, uses a domain not belonging to SendGrid.
- Recipients are informed that their services have failed to renew and are about to expire. They are directed to update their billing information to rectify the issue.
- Users who click the link are led to a fake a SendGrid login page. Once their details are submitted users are redirected to the real SendGrid page.
MailGun Phishing Email
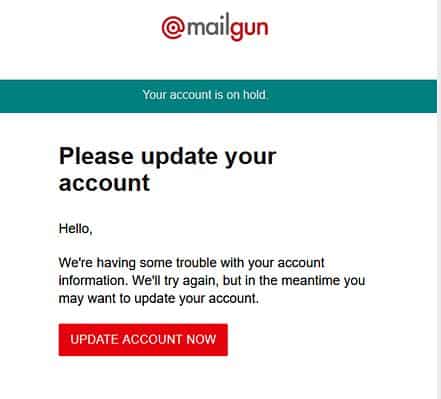
- Claims to be from email service provider MailGun , this email is titled “Your account is on hold”.
- Uses the display name “Support MailGun” and employs MailGun branding. However this email is actually sent from a compromised account.
- Users are informed of some issues with their account information and includes a link to update their account.
- Recipients who click the link are led to a fake login page employing MailGun’s branding. The domain used does not belong to MailGun, exposing its illegitimacy.
- Once users login to their account their details are collected and they are redirected to the real MailGun website.
‘Purchase Order’ Phishing Email
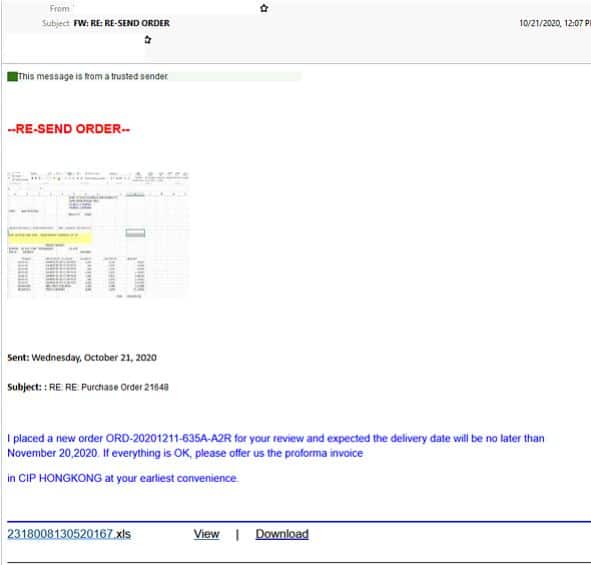
- Purporting to be a purchase order alert this email is designed to look like an auto generated notification
- The email employs a ‘ Trusted Sender” header and asks recipients to ‘resend order’ and provides them with a link to do so.
- Users who click the link are redirected to a page that appears to be hosting a blurred Microsoft Excel file and are then met with an Excel branded login Window where they are directed to login in order to view the document.
- Once the recipient submits their details they are met with an ‘access denied’ error message and are redirected to a website with the domain portion of the email.
‘Pay Slip Invoice’ Phishing Email
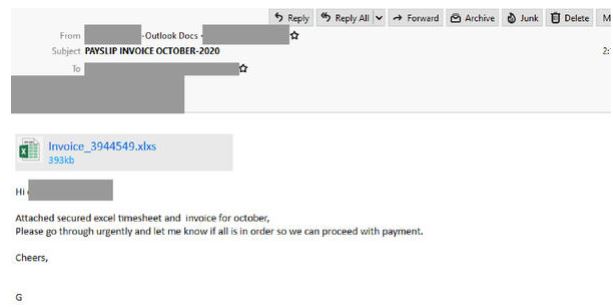
- Titled “PAYSLIP INVOICE OCTOBER – 2020”. Recipients are alerted to urgently view an “attached secured timesheet and invoice for october” to proceed with payment with a link to the invoice provided masquerading as a Microsoft Excel attachment.
- By clicking the link unsuspecting recipients are led to a silent redirected page hosted on a compromised site before being presented with a blurred Microsoft Excel page with a login window employing the Excel branding directing them to login to view the file.
- Once the user logs in they receive an error message informing them the credentials they entered are invalid.
DHL Phishing email
- Impersonates global logistics service DHL and uses the display name “DHL Express”.
- Titled “DHL On Demand Delivery”. It informs recipients of an undelivered package from the DHL office and directs them to go online to submit their correct address with a link provided for them to do so.
- The email address used in the from field is not a valid DHL address and is actually from a compromised mail server.
- The email employs DHL’s branding and logo, with a footer containing a ‘confidentiality notice’ and claims to be an automated message from DHL Management.
- Recipients who click the link are presented with a fake DHL login page, with their email address already filled out.
- Once users enter their password and login they are met with an error message informing them the login failed.

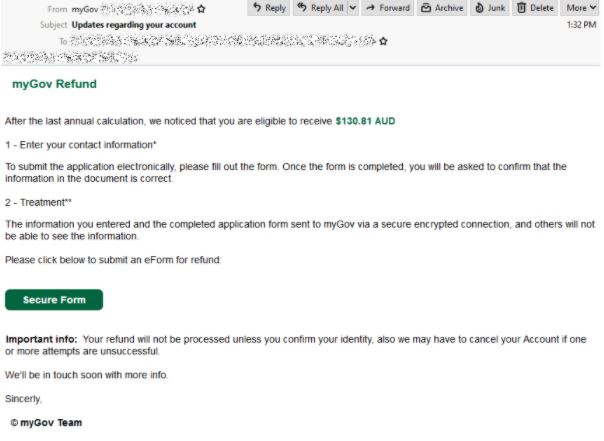
myGov Phishing Email
- Masquerades as government services portal myGov, the subject reads “Updates regarding your account” .
- This email uses the display name ‘myGov’ but is sent from an email address using a domain that does not belong to myGov.
- It informs users that they are “eligible to receive $130.81 AUD” and they need to submit an ‘eForm’ to claim their refund.
- A secure form button is provided , with the use of a URL shortener to hide its destination. An ‘important info’ section is provided informing users that their refund will not be processed until they confirm their identity.
- Clicking the ‘secure form’ button leads users to a fake myGov login page which appears to be a very good replication of the real page but the domain used doesn’t belong to myGov or the Australian government, indicating that this is not a legitimate page.
- When users sign in to their accounts they are redirected to a new page requesting personal details like full name, date of birth and home address. From here users are brought to another page asking them to submit their credit card details.
- Once their credentials are entered the user is led to a final page informing them their details are being processed and to not close the window.
Compromised Outlook Account
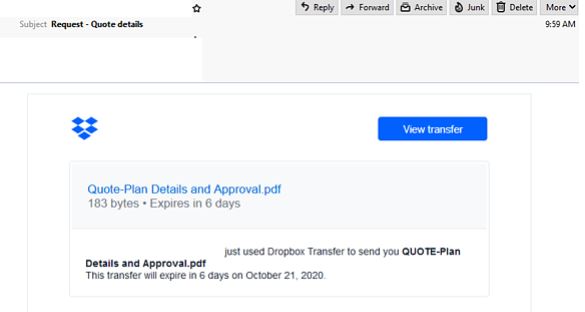
- A compromised Outlook account is sending malicious emails, masquerading as a Dropbox notification. Titled “Request – Quote details”.
- This email employs Dropbox’s logo and colour palette and informs the recipient that a new PDF file that expires in six days has arrived.
- A link is provided for recipients to view the file which upon being clicked takes the users to a fake Adobe PDF Online login page. Although the page contains Adobe’s logo it is hosted on a domain that does not belong to Adobe.
- Once users submit their credentials they receive an error message saying “InValid Credentials”
If you’d like any further information, assistance with your cyber security or you don’t know where to start, please call us on 1300 478 738 or Email us.




