Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
You need to be particularly aware of:
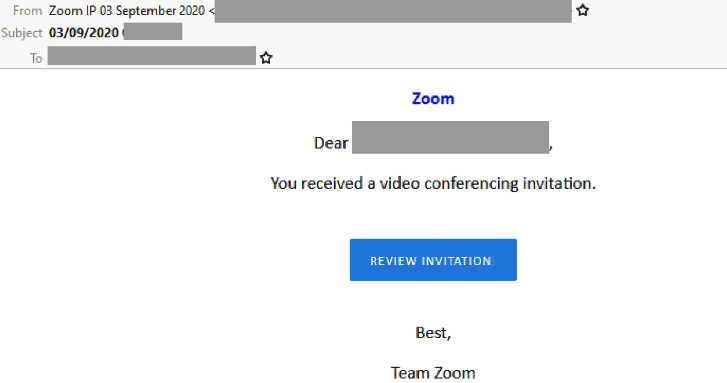
Zoom Phishing Email
- This latest phishing email is titled ‘Reminder: Your meeting attendees are waiting. Monday, August 24, 2020′. The display name it uses is ‘Zoom’ and uses a domain not belonging to Zoom.
- Recipients who click the ‘Review invitation’ link are directed to a fake Microsoft-branded login page and asked, “sign in to Zoom with your Microsoft 365 account”.
- After logging in the site prompts users to verify their password due to a ‘sign in attempt timeout’. After inserting their password 2-3 more times users are sent to another page informing them that “this video conferencing has been cancelled”.
- The purpose of this phishing scam is to gain access to your data.
- Although cyber criminals try to make these emails appear real by using the display name ‘Zoom IP’ and the addition of the Microsoft logo and branding elements to trick users into believing the email is real.
- Red flags in this scam include: Spelling errors, unfamiliar domain in the ‘from’ field, and phishing pages are not hosted by either Zoom or Microsoft domains
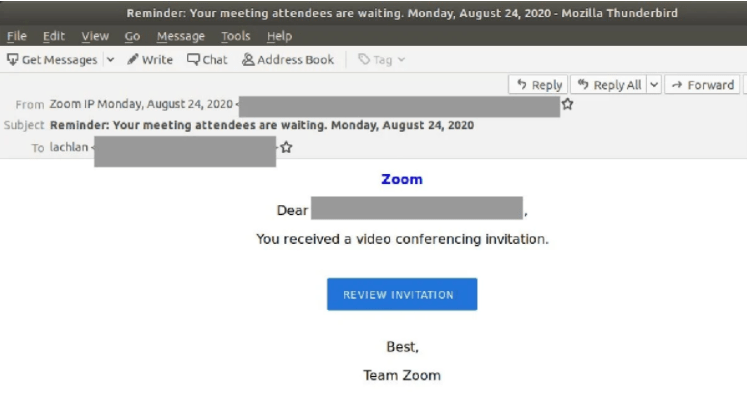 Another Zoom phishing scam posing as a Zoom meeting invitation has been discovered. This email originates from an Amazon SES account.
Another Zoom phishing scam posing as a Zoom meeting invitation has been discovered. This email originates from an Amazon SES account.- Like the Zoom phishing scam discussed above, this email redirects users to a fake Microsoft-branded login page. This page asks users to sign in to Zoom with their Microsoft 365 account, and the attacker collects this information.
- This site is not hosted by either a Zoom or Microsoft domain but what appears to be a compromised Oracle cloud hosting account.
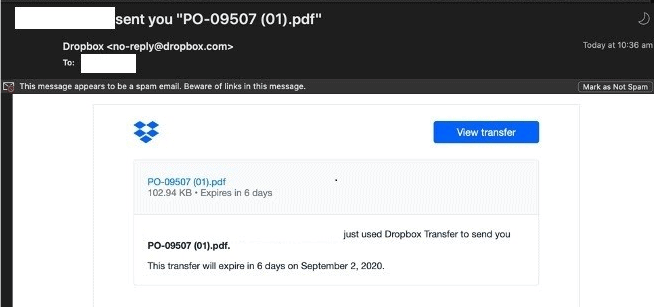
Compromised Dropbox accounts
- A scam email from a compromised Dropbox account informs recipients they have received a P.O. in the form of a PDF file.
- Email security services are unlikely to block these emails because they are coming from real accounts.
- The PDF file directs users to external phishing pages to harvest credentials.
- Users should not open emails from Dropbox if they are not expecting files from the sender and to forward it to abuse@dropbox.com if they are unsure if the email is a real notification from Dropbox.
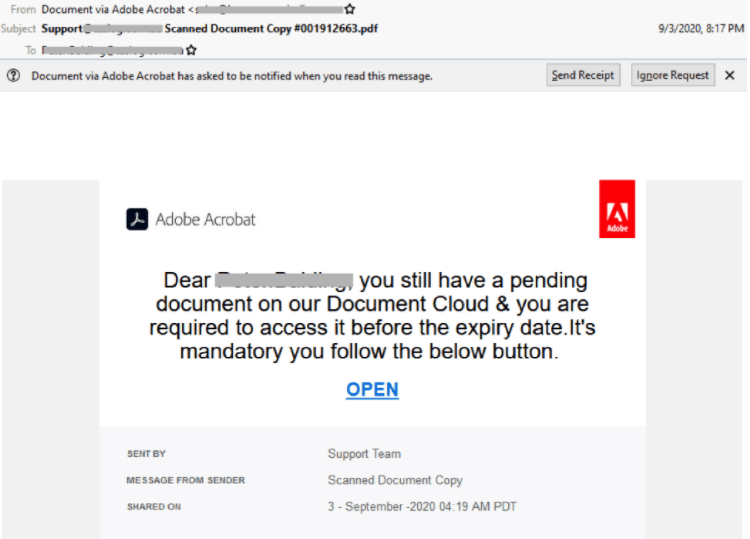
Adobe Creative Cloud Service Phishing Email
- Emails claiming to be from Adobe Document Cloud may be the latest scam attempting to harvest sensitive user data.
- This email tells the recipient they have ‘a pending document’ that ‘requires them to access it before the expiry date’ and that it’s ‘mandatory they follow the below button.’
- To improve engagement the subject line and the content of the email feature the recipients’ company and name.
- The email comes from multiple compromised accounts in Bangladesh and India.
- Informs recipients that a “secured document” has been shared using “Adobe Creative Cloud Service”.
- The ‘OPEN’ link sends users to an Adobe Acrobat page prompting them to ‘Download’ and ‘Logon with your own email and password.’
- Email users should be wary of emails they receive from Adobe Document Cloud and of messages from unfamiliar senders requesting they log into their accounts.
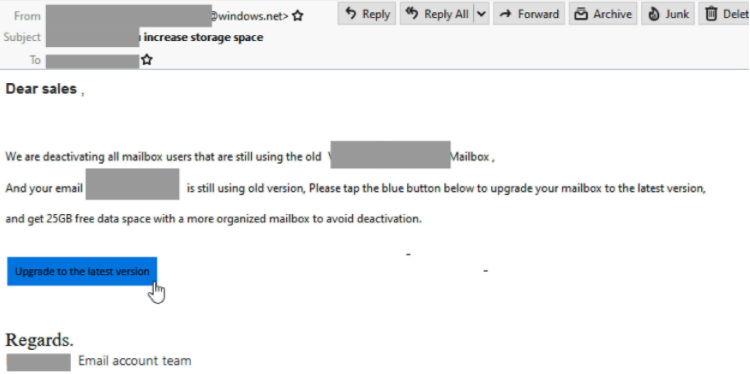
LinkedIn brand-jacked
- A phishing email claiming to be a notification from users ’email account team’ has been found.
- This email advises users they will deactivate the users email account unless they upgrade to “the latest version”.
- However, this button reveals a LinkedIn URL. When users click this URL, it sends them to a phishing page that asks for their email username and password.
- The attacker collects the user’s credentials for later use.
- The use of the LinkedIn URL is likely an evasion tactic to bypass email security filters.
- Many trust the LinkedIn brand, so seeing a URL using a LinkedIn domain is not likely to raise much suspicion.
- Users should be skeptical of messages from unfamiliar senders asking them to log into their accounts.
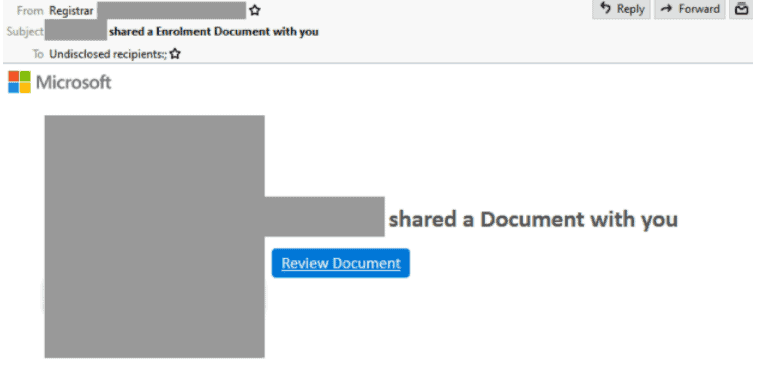
Microsoft phishing email
- There is malicious email in the form of a file-sharing notification from a compromised account going around.
- The email invites recipients to review the document. This sends users to a page containing a ReCAPTCHA form and Microsoft’s logo.
- Once users fill out the ReCAPTCHA they are led to a fake Microsoft login page. This page requests their email address and password.
- The attacker collects the user’s credentials for later use.
- The ReCAPTCHA feature is likely an evasion tactic to evade automated link checking by email security filters.
- Users should always be wary of emails from unfamiliar senders asking them to log into their accounts.
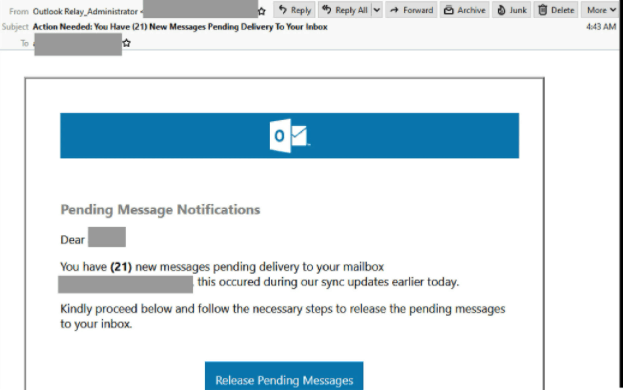
Outlook Phishing email
- Email users should be wary of a phishing email posing as a ‘pending message notification’. This email, titled “Action Needed: You have (21) New Messages Pending Delivery to Your Inbox”. It claims to be an automated email from the recipient’s mail server.
- This email uses the display name “Outlook Relay Administrator” and utilises Microsoft Outlook Web Access branding. However, the email address in the “from:” field does not use a domain belonging to Microsoft, or the recipient’s company. The email originates from a compromised third-party account.
- This email prompts recipients to click to release their pending messages. From here a fake Microsoft Outlook login page will ask users to sign in.
- The attacker collects the user’s credentials for later use.
- There are a few red flags in fake emails users should look out for such as: minor grammatical errors and the use of a suspicious domain in the ‘from’ section of the email.
If you’d like any further information, assistance with your cyber security or you don’t know where to start, please call us on 1300 478 738 or Email us.