Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include:
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
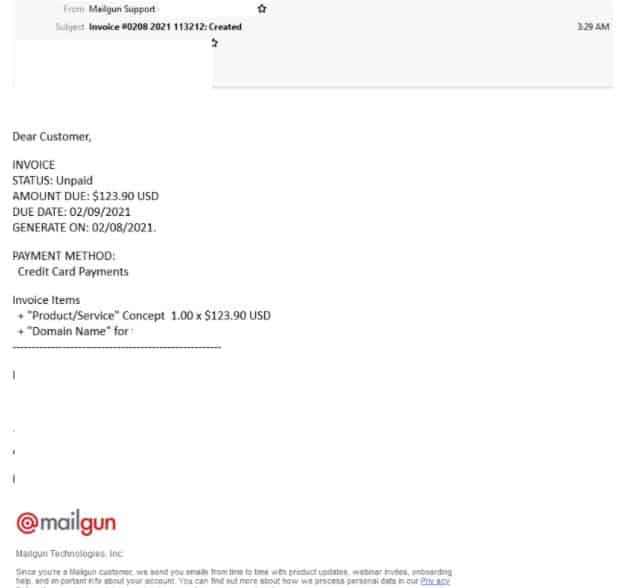
MailGun Phishing Email
- This phishing email purports to be from Mailgun Technologies and uses the display name “Mailgun Support”.
- The subject contains an invoice number and the body of the email contains details such as the amount due and when the invoice was generated, along with a link for the recipient to view the invoice.
- The email employs Mailgun’s logo and a footer containing Mailgun related links and details.
- Clicking the link to access this invoice leads to a fake login page which uses Mailgun’s branding elements but is not actually hosted on a domain belonging to Mailgun but a compromised WordPress site.
- Once the user enters their credentials to log in they receive an error message saying these details are invalid, after multiple attempts they will be redirected to the real Mailgun page.
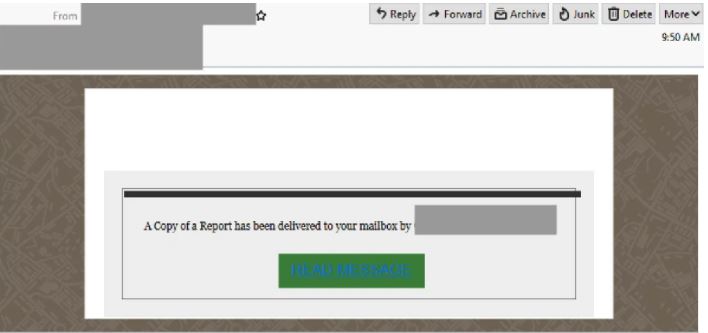
Office 365 Phishing Email
- Masquerading as an automatic file sharing alert this email comes from a compromised account and claims to be a copy of a report sent from the Operations officer of a company based in Australia.
- Recipients are encouraged to click the link included to view the report, however, clicking the link leads to a login page employing the Office 365 logo and branding elements to appear as a legitimate page, here users are to ‘sign in to continue’ with a field provided for them to submit their email address.
- Once the users email address is submitted they are led to a new page which requests their passwords, however on this page, the logo of the user’s email service provider is displayed.
- Once their details are submitted the user receives a message that the details they have submitted are invalid.
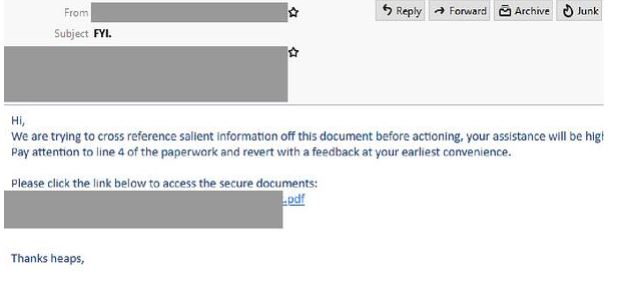
‘Secured documents’ Phishing Email
- This phishing email comes from a compromised account of an Australian finance worker and is titled: FYI.
- Claiming to attempt to cross reference salient information, the sender requests the recipients view the attached paperwork and ‘revert with a feedback’, with a link provided for the recipient to access the ‘secure documents’.
- Clicking the link provided opens what appears to be a webpage for a document sharing site where users are informed of a pending document awaiting their review which uses the Adobe PDF logo.
- Recipients who click to review the document are led to a login page which employs the branding elements of Dropbox and office 365, however the URL used is hosted on a domain not belonging to Dropbox or Microsoft.
- Once signed in the user is met with an error message saying the details they have entered are invalid.
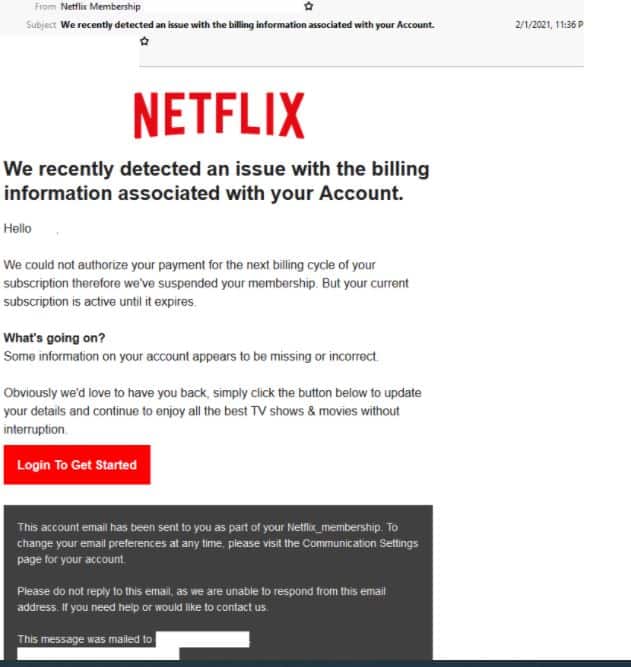
Netflix Phishing Email
- Masquerading as popular streaming service Netflix, this email is titled ‘We recently detected an issue with the billing information associated with your Account’.
- The email employs some of Netflix’s branding elements and uses the display name “Netflix Membership”, however the sender’s email address is not hosted on a domain belonging to Netflix.
- The recipient is informed that ‘payment for the next billing cycle’ of their subscription could not be authorised causing their membership to be suspended.
- The user is then advised to update their details via the “login to get started” button provided.
- By clicking the link recipients are led to a login page designed to look like a legitimate page belonging to Netflix, however the domain used in the page’s URL doesn’t belong to Netflix.
- Once the user submits their login details they are led to a page requesting their preferred method of payment which then leads to another page where they are asked to submit their credit card details.
- Recipients are then led to a Netflix-branded confirmation page informing them that Netflix has ‘restored access’ to their account.
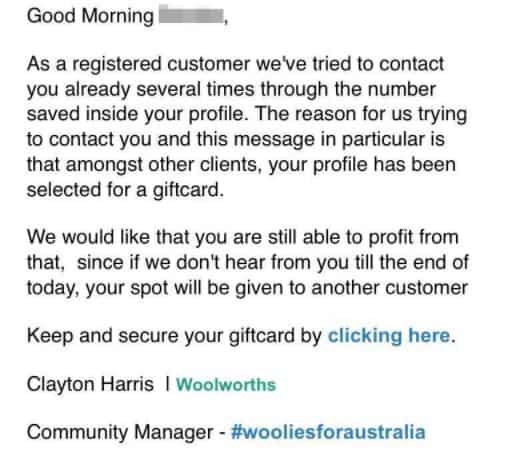
Woolworths Gift Card Scam
- Claiming to be from Woolworth’s community manager, this email promises the recipient a Gift card in a poorly worded email.
- The recipient is informed that the team at Woolworths has been trying to contact them several times to present them with the gift card but has been unsuccessful, because of this ,if the customer doesn’t respond before the end of the day they forfeit their gift card to another customer.
- A link is provided for the recipient to ‘keep and secure’ their gift card which leads to a page requesting the user submits their personal information in order to receive this gift card.
- A Woolworths representative confirmed that this is a scam email and is in no way affiliated with the real Woolworths and should not be engaged with.
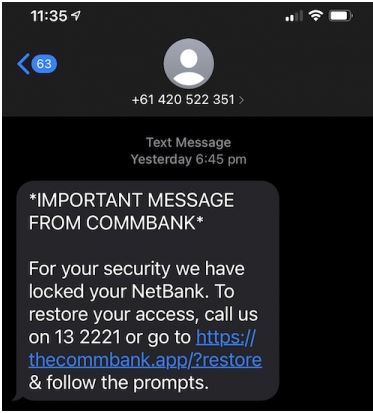
CommBank Phishing SMS
- Purporting to be a security alert from the Commonwealth Bank and titled *IMPORTANT MESSAGE FROM COMMBANK*, this SMS informs the recipient that for security reasons their NetBank has been locked and provides a link for them to restore access to their account.
- Clicking the link provided leads to a fake login page which employs the logo and branding of the Commonwealth Bank.
- Here the user is requested to follow the prompts and submit their username and password.
- Once these details are entered the user receives an error message informing them their credentials are invalid.
If you’d like any further information, assistance with your cyber security or you don’t know where to start, please call us on 1300 478 738 or Email us.




