Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include:
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
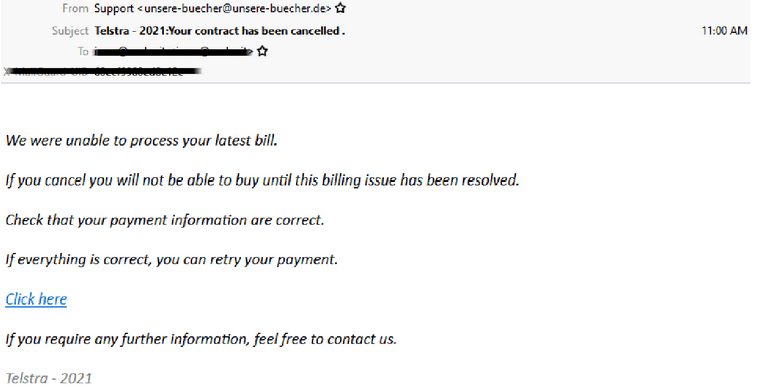
Telstra
- Telstra is being impersonated in this latest phishing scam in attempt to obtain sensitive credentials.
- Sent from ‘Support’ using a compromised website in Germany, it advises recipients that ‘Your contract has been cancelled’ and “We were unable to process your latest bill”
- A link is provided to try and get users to retry payment.
- Once the link is clicked, users are redirected to a fake but credible looking Telstra branded web page which attempts to capture usernames and passwords.
- Other details requested include, credit card details including name, card number, expiry, CCV and mobile number.
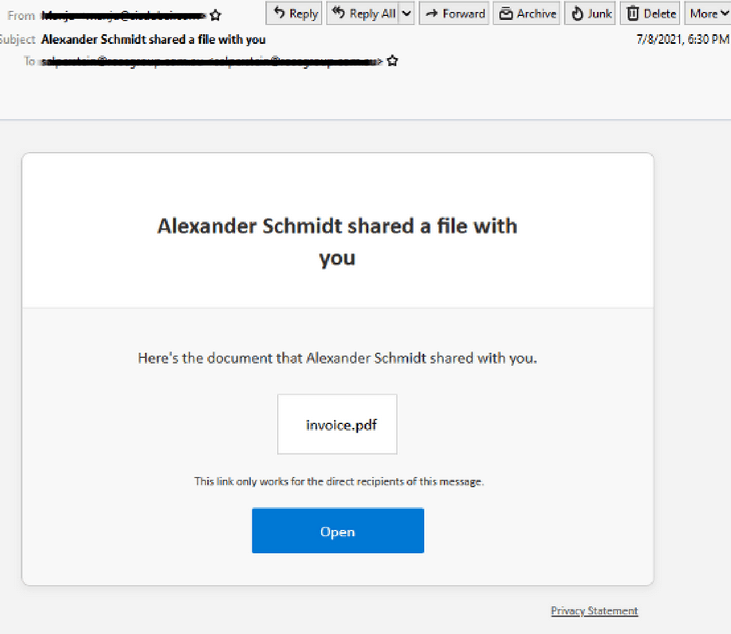
OneDrive & Outlook File-Sharing
- Designed to harvest credentials, this latest scam email uses a Microsoft OneDrive template and is linked to 2 different phishing pages.
- Sent from a compromised account which is owned by “Sabari Indian School”, whilst the phishing page is on a Digital Ocean App platform domain which is spoofed using Cloudflare.
- The links contained in the email, redirect to 2 phishing pages, the first using company branding and the second carries Outlook AWA branding.
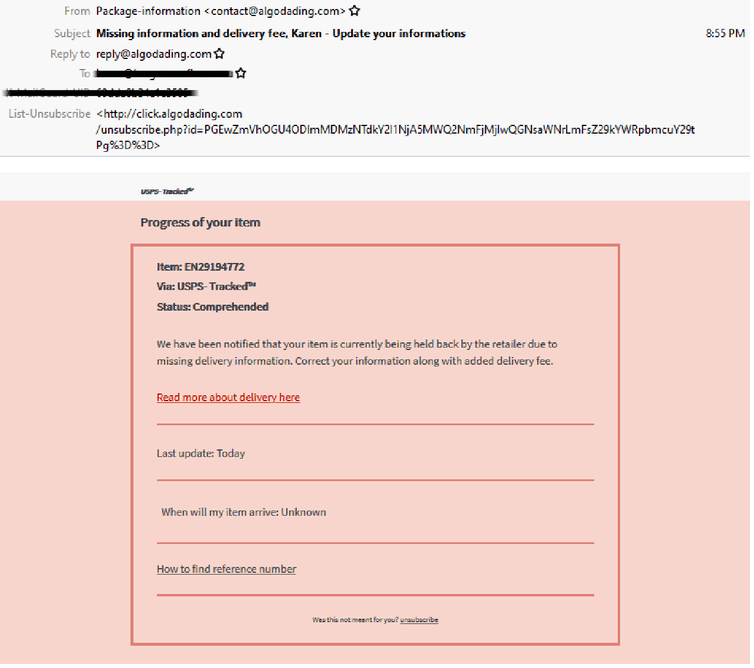
USPS
- Sent using the subject “Missing information and delivery fee, (name) – Update your informations and with USPS Branding, it is designed to harvest personal information.
- Claims that the item has been held back and to correct your information along with an added fee.
- Comes from a server hosted by Digital Ocean and uses an intermediary page that takes users to a series of web and credit card payment pages.
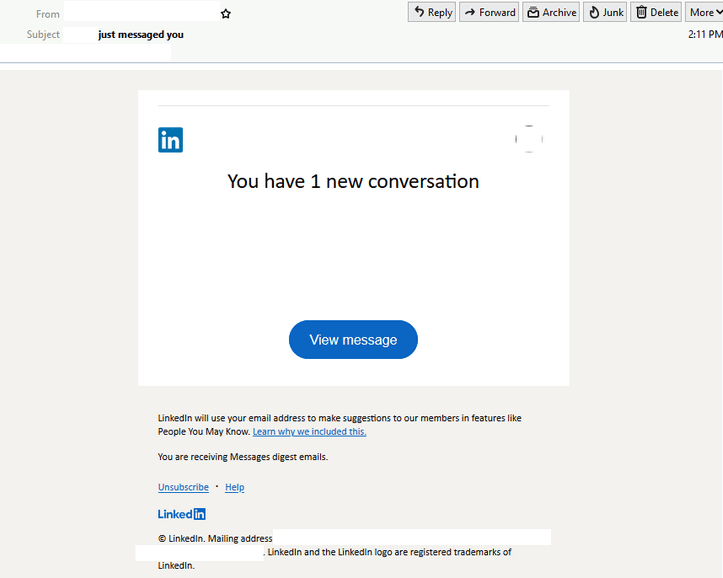
- Designed to harvest confidential data for malicious intent.
- Masquerades as an auto-generated notification to inform recipients about a message that has been received.
- Contains LinkedIn branding elements to boost its legitimacy.
- ‘View Message’ button redirects to a login page requesting LinkedIn credentials.
- Phishing page is hosted on a SaaS website development platform – pantheon.io
Microsoft SharePoint
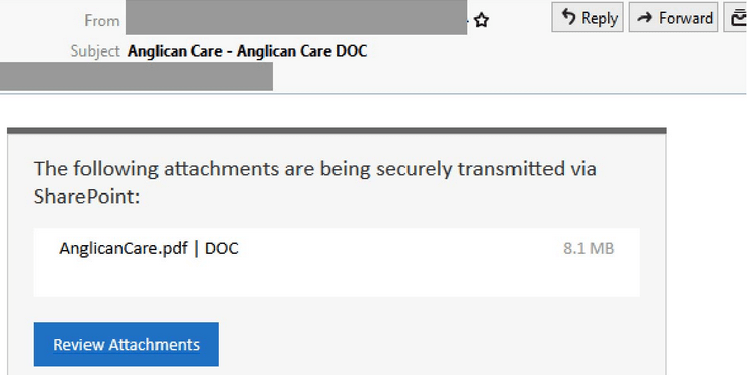
- Sent from a compromised account belonging to a user at Anglican Care and titled “Anglican Care – Anglican Care DOC”.
- Masquerades as a document alert for a file being sent using SharePoint.
- The email contains a link to a .PDF file which when clicked redirects to an intermediary site requesting another link be clicked.
- Users are requested to provide data such as email addresses & passwords on URLs that don’t belong to Microsoft or Anglicare.
DHL
- Uses DHL branding, a display name of “DHL express” and is titled “Package tracking:”
- Advises recipients that they have a “package pending in Terminal 1” and to pay a shipment fee within 48 hours to complete delivery.
- Those who click the link are redirected to a webpage whereby personal information is requested such as name, address, email, credit card information and phone number.
- If all requested information is provided, users are met with a prompt supposedly from their bank.

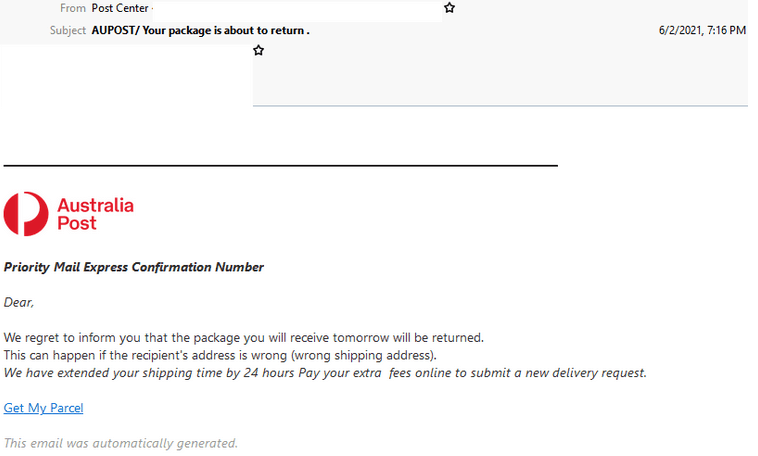
Australia Post
- Uses Australia Post branding, a display name of “Post Centre” and is titled “AUPOST/Your package is about to return.”
- Sent from a potentially compromised Plesk server hosted overseas.
- Recipients are informed that a package will be returned due to a “wrong shipping address” and are direct to pay ‘extra fees’ via a “Get My Parcel” link.
- Those who click on the link are led to phishing pages whereby personal details including credit card information is requested.
- After details are provided, users are prompted for a verification code that has supposedly been sent to their mobile.