Business cyber security measures should be an essential part of COVID-19 business contingency planning
With more and more staff working from home in Australia due to COVID-19 measures, cyber criminals have already started taking advantage of vulnerabilities arising from the use of remote access technologies. This means it’s essential to incorporate good cyber security measures into your contingency and business continuity planning.
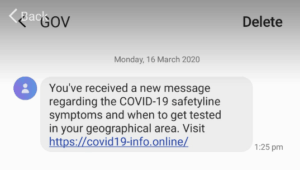
The Australian Cyber Security Centre (ACSC) has reported a COVID-19 themed scam being distributed via text message. The message appears to come from ‘GOV’ as the sender
and includes a SCAM link that if clicked, may install malicious software on your device, designed to steal bank details.
Cyber Security Measures Your Business Should Undertake
Being proactive and ensuring good cyber security measures is the best way to address cyber threats. We recommend the following measures:
1. Review your Business Contingency plans and procedures.
Our COVID-19 business continuity checklist can help you plan.
2. Ensure your systems are up-to-date
This includes ensuring your networks and firewalls are up to date with the most recent security patches
3. Increase Cyber Security Measures
Increase these measures in anticipation of the higher demand on remote access technologies. Don’t forgot to also test these measures ahead of time, if possible
4. Remote Desktop Client
If you use a remote desktop client, ensure it is secure.
5. Remote Devices
Ensure all work devices including laptops, mobiles and tablets, are secure.
6. Backups
Ensure that servers are still being backed up and staff, if they are using systems remotely but saving locally, are backing up their work securely.
7. Multi-Factor Authentication
If you haven’t already done so, implement multi-factor authentication on all remote systems and resources. This includes your Cloud-based services.
8. Educate Your Staff
Ensure your staff are educated about good cyber security practices, such as detecting socially-engineered messages.
If you have any questions or concerns about your cyber security or business IT, contact Surety IT today.
Further Reading
How to Protect Your Business from Ransomware
What to include in a Laptop Security Policy




