Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include;
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
Microsoft Phishing Email
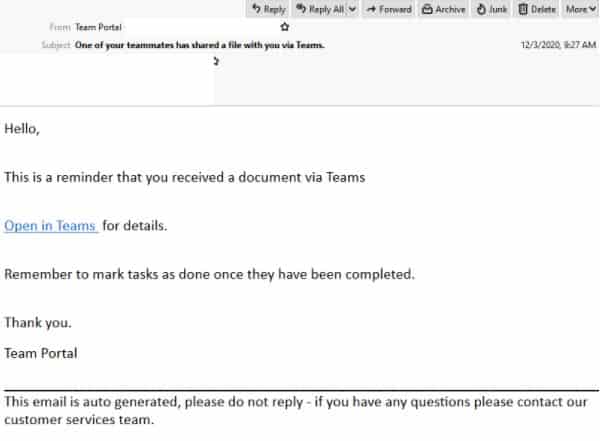
- Masquerading as popular online collaborative platform, Microsoft Teams, this email is titled: “One of your teammates has shared a file with you via Teams”.
- This email employs the display name ‘Team Portal’ but does not contain any Microsoft related branding elements or logos.
- It alerts recipients that they have received a document via Teams and includes a link for them to view the document.
- Clicking the link leads to an intermediary page which contains details about the file and contains the Microsoft Team’s logo and branding elements, however this page is hosted on a domain not belonging to Microsoft.
- On this page there is a link provided to preview, download or open the document. Clicking this link leads the user to a fake Microsoft branded login page which is actually a compromised WordPress site.
- Once the user submits their credentials , they are met with a message informing them these details are invalid.
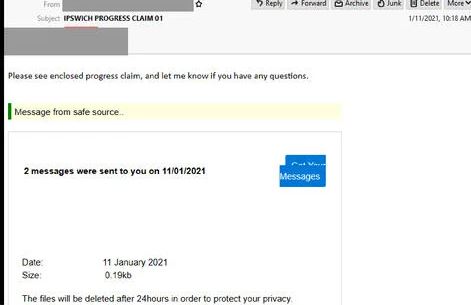
- Another Microsoft related phishing email to be cautious of is titled: “Ipswich Progress Claim 01” this email claims to be a progress claim alert and is sent from a compromised account belonging to a COO of an Australian-based company.
- Recipients are invited to view an ‘enclosed progress claim’ which informs users that two messages were sent to them 11th January 2021, with a link provided to view these messages and a disclaimer that these files will be deleted after 24 hours to protect the recipient’s privacy.
- Clicking the link provided leads to a login page which employs an altered version of the Microsoft Office logo and requests they verify their account. However, the URL used by this page is hosted on a domain not belonging to Microsoft.
- Once the user has submitted their email and password to ‘verify’ their account they receive an error message which claims the credentials submitted are invalid.
Outlook Phishing Email
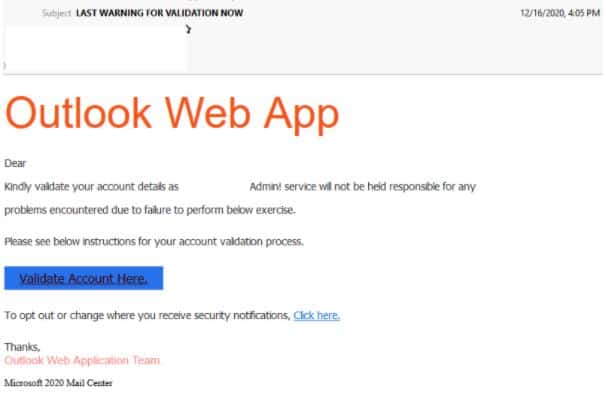
- Titled “Last Warning For Validation Now”. This phishing email purports to be a security notification from the Outlook Web Application.
- The email instructs users they need to validate their account and informs them their admin service will not be held responsible for any issues, if they fail to do so, providing a link for them to validate their account.
- It ends with the sign off from the ‘The Outlook Web Application Team” accompanied with a footer which claims the email is from the ‘Microsoft 2020 Mail Center’, however the email used by the sender is not hosted by a domain owned by Microsoft or the recipient’s company.
- Clicking the email leads users to a login page which requests their email and password.
- Once users submit theses details they are redirected to the website associated with their domain.
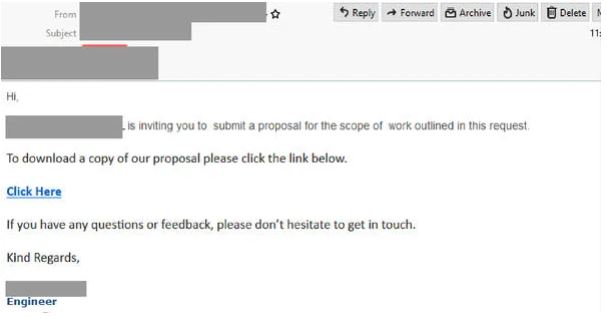
- Another Outlook related phishing email to be aware of invites recipients to ‘submit a proposal for the scope of work outlined in this request’, with a link provided for the user to download a copy of the aforementioned request.
- Clicking the link in the email leads to an intermediary page which employs the branding and logo of the company mentioned in the email, accompanied by another link which encourages the users to ‘Click here to get C-T terms and requirements’.
- This link leads to a fake Microsoft Outlook login page which uses Microsoft’s logo but is not hosted on a domain belonging to Microsoft.
- Once logged in the user is met with an error message informing them these credentials are invalid.
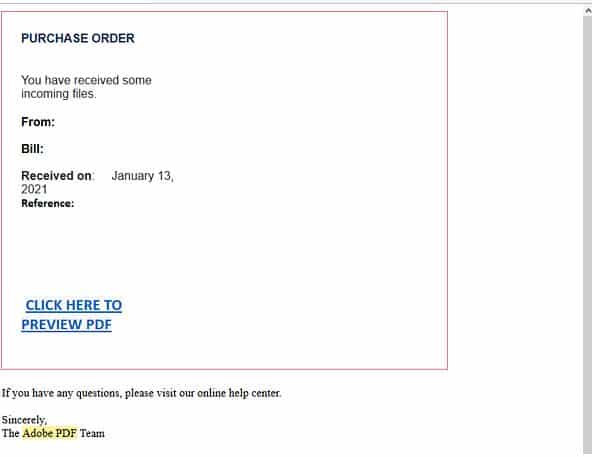
Adobe Phishing Email
- This phishing email purports to be an automated alert for a purchase order. The alert includes multiple details pertaining to the purchase order including the date it was received, who sent it and a reference number, however, this email was sent from a compromised account belonging to a legitimate company’s representative.
- A link is provided for the user to ‘preview PDF’ and signs off from ‘The Adobe PDF Team”.
- Recipients who click the link are sent to an intermediary page containing the details of the purchase order, titled: Sign-In Secure Document.
- This page employs Adobes logo and uses a signature belonging to the representative mentioned in the email, yet the URL used is hosted on a domain which does not belong to Adobe or the representative’s company.
- Clicking to “Review Document” leads users to another page which has it’s background blurred. In the forefront a message appears which uses both Adobe and Microsoft’s branding, and requests that they choose their preferred account and login to read the document.
- Once users log into their account they receive a message stating the credentials they submitted were invalid.
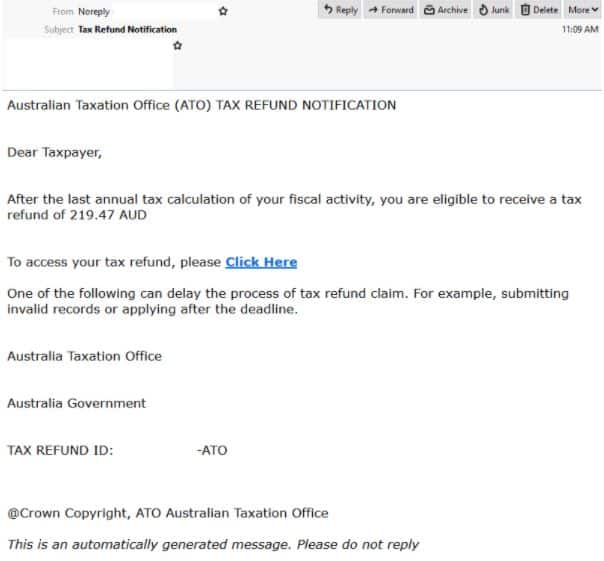
myGov Phishing Email
- This email purports to be from The Australian Taxation Office and is titled: “Tax Refund Notification”.
- It appears to be an automated notification and employs the display name ‘Noreply’.
- Addressed to the “Taxpayer”, this email informs recipients that they are eligible to receive a $219.47 AUD tax refund. A link is provided for the recipient to access their refund and a warning that their claim may be delayed due to “submitting invalid records or applying after the deadline”.
- Clicking the link leads recipients to a login page which employs the same branding and logo as the legitimate myGov login portal.
- Users are instructed to sign into myGov using their email account. However, the URL used by this page is not hosted on a domain belonging to myGov or the ATO.
- Once the user logs into their account they receive an error message that their credentials were invalid.
DHL Phishing Email
- Masquerading as popular international delivery service DHL this email is titled: ‘Confirm your package’ and uses the display name ‘package-team’.
- The email notifies the recipient that their package has arrived at their local post office “But hasn’t been delivered yet” and requests they “pay 1.99$” if they wish to confirm and view the shipping details, with a link provided for them to do so.
- The email employs the logo and branding elements of DHL the email address used by the sender does not appear to be a valid DHL address and the email contains multiple grammatical errors.
- Clicking the provided link leads users to a page which also uses DHL’s branding and includes a reCAPTCHA feature so the user can ‘verify they are human’.
- Completing the reCAPTCHA then takes the user to a new page which requests their credit card details.
- Once they submit these details, the user receives a message which states their request is being processed with their banks and they are to keep the window open.

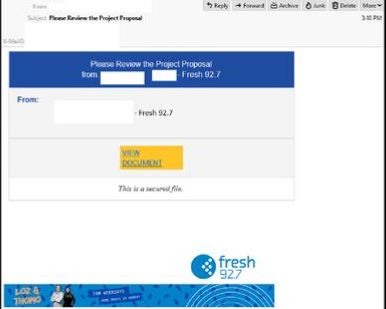
Fresh 92.7 Phishing Email
- Claiming to be a file-sharing notification from a representative at Fresh 92.7 this email is titled: “Please Review the Project Proposal” and includes a link for the recipient to view the document.
- Clicking this link leads users to a login page which employs many branding elements of Microsoft products and the header ‘OneDrive’, however the URL used is not hosted on a domain belonging to Fresh 92.7 or Microsoft.
- Once the users have logged in they receive a confirmation message which states they will be contacted within 48 hours.
If you’d like any further information, assistance with your cyber security or you don’t know where to start, please call us on 1300 478 738 or Email us.




