Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
You need to be particularly aware of:
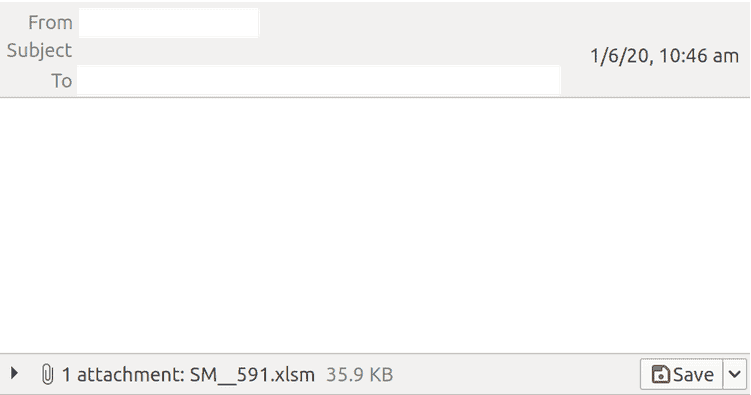
1. Fraudulent Emails using Excel attachments
- Sent with no subject or text in the email body, this fraudulent email uses a malicious payload disguised as a Microsoft Excel attachment.
- Originates from a large number of different email address, likely to be compromised accounts.
- Once recipients enable macros/ additional content to be run, the malicious code is executed.
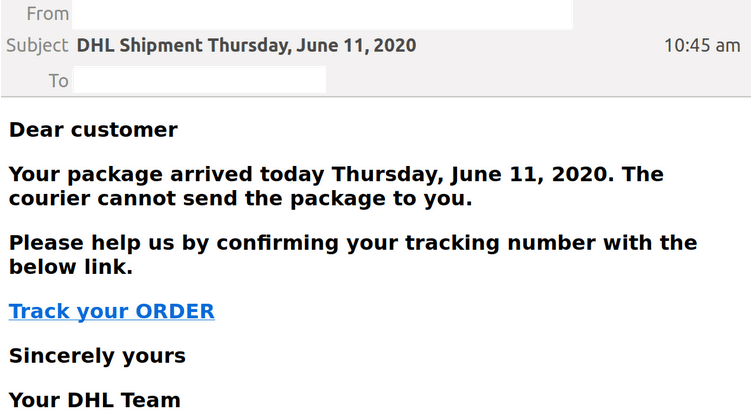
2. DHL Spoofed
- Purports to be from DHL, titled “DHL Shipment Thursday, June 11, 2020 & includes the recipients email address in the “from” field.
- Sent from a compromised email account, it informs recipients that “the courier” is unable to send a package that “arrived today”
- Requests confirmation of tracking number via a link which leads to a DHL branded phishing page.
- Should the link be clicked, personal details are requested, such as full name, address & phone number and upon submission, recipients are advised that an error has occurred and they are redirected to the actual DHL website.
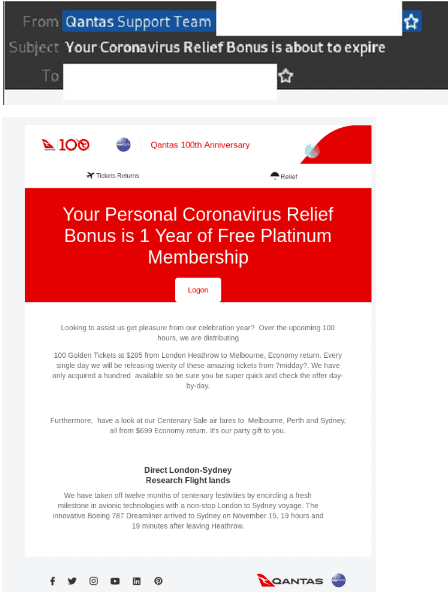
3. Qantas Spoofed: “Coronavirus Relief Bonus”
- Titled “Your Coronavirus Relief Bonus is about to expire”, originates from several email addresses belonging to different domains and uses multiple display names.
- Containing Qantas logo and branding within the body of the email, recipients are provided with a button to login and claim the bonus.
- The button directs recipients to a phishing page that appears as a Qantas Frequent Flyer login page.
- Personal details such as membership number, last name and security PIN are requested and those who provide these details are taken to another page which displays the error “the details do not match our records”.
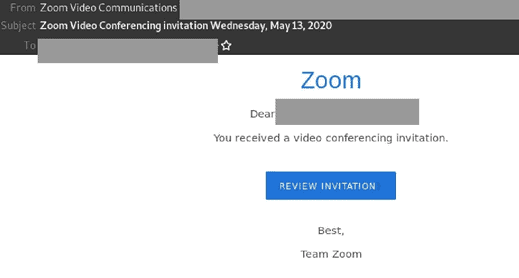
4. Zoom Video Conferencing Invitation
- In attempt to obtain confidential information, an email purporting to be from Zoom is hitting inboxes.
- Sent using a display name of “Zoom Video Communications”, the email is titled “Zoom Video Conferencing invitation Wednesday, May 13, 2020 and originates from multiple randomly generated email addresses hosted on amazonses.com
- Within the body, the email is directed to the email address displayed in the “to” field and informs recipients that they have received a video conferencing invitation.
- Upon clicking the button to “review invitation”, the recipient is led to a fake Microsoft-branded login page whereby they are requested to sign in to Zoom with your Microsoft 365 account which is not hosted on either a Zoom or Microsoft domain.
- Once “logged in”, the recipient receives an error “sign in attempt timeout, verify your password to access Zoom invitation” whereby on submission of the password on a 2nd attempt, recipient is redirected to the legitimate Zoom home page.
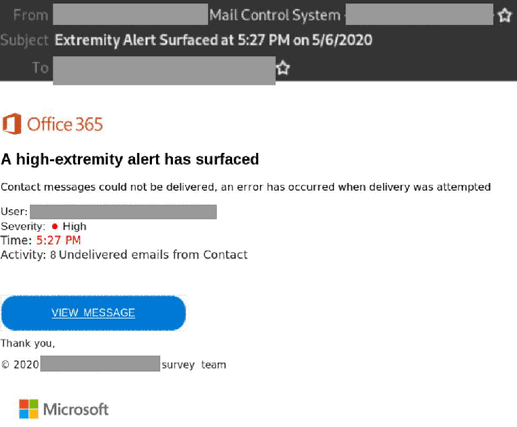
5. Microsoft Office 365 Spoofed
- Microsoft Office 365 have been brand-jacked in an attempt to obtain confidential information.
- Using the domain of the recipient’s email address as a prefix, the display name also contains the words “Mail Control System”
- Titled “Extremity Alert Surfaced” followed by a time stamp, the email originates from a single compromised email address and contains Office 365 logo and branding.
- Those who click on the “View Message” link are redirected to a fake Microsoft Office 365 branded login page which is a phishing page hosted on a domain not belonging to Microsoft.
- To verify identity, CAPTCHA is required first followed by entry of password which prompts are “wrong password” error message.
- Upon entering the password a 2nd time, users receive account verification confirmation and are redirected to the authentic Office 365 login page.
If you’d like any further information, assistance with your cyber security or you don’t know where to start, please call us on 1300 478 738 or Email us




