Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include;
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
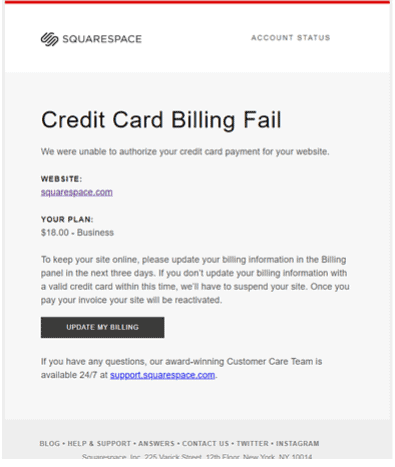
SquareSpace Phishing Email
- Impersonates popular web host & website creator Squarespace. The subject reads: ‘Final Notice – Failed billing method’.
- Uses the display name ‘Squarespace [ALERT] ‘ and begins with ‘squarespace-alert’. However, the email address uses a domain not belonging to SquareSpace.
- SquareSpace logo is cut-off which highlights it’s illegitimacy.
- Email begins with the header ‘Credit Card billing Fail’. It informs recipients that authorisation of credit card payment for their website cannot proceed and are given 3 days to update billing information to prevent the suspension of their site.
- Clicking the link to update their billing details leads to a phishing page whereby they are requested to login to their SquareSpace account.
- Once the user enters their information they receive an error message saying the password is incorrect.
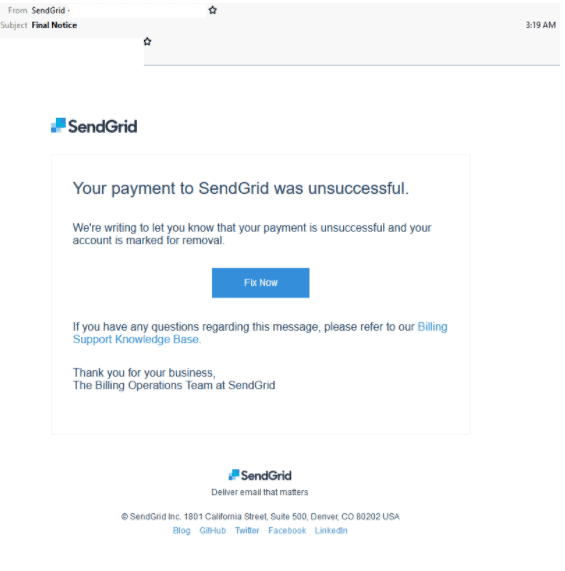
Compromised SendGrid Account
- Sent from a compromised SendGrid account employing the title ‘Final notice’.
- Poses as a billing alert from the popular email service.
- Informs users their ‘payment to SendGrid was unsuccessful’ and to click a link to fix.
- By clicking this link it redirects users to a fake SendGrid login page which requests their username and password.
- Convincing recreation of a legitimate SendGrid login page; however with minor differences in text styling and hosted by Google Firebase.
- Once users login they are sent to a SendGrid support page about how to interpret their invoices.
- Email security filters are unlikely to detect phishing emails from compromised accounts making them particularly dangerous.
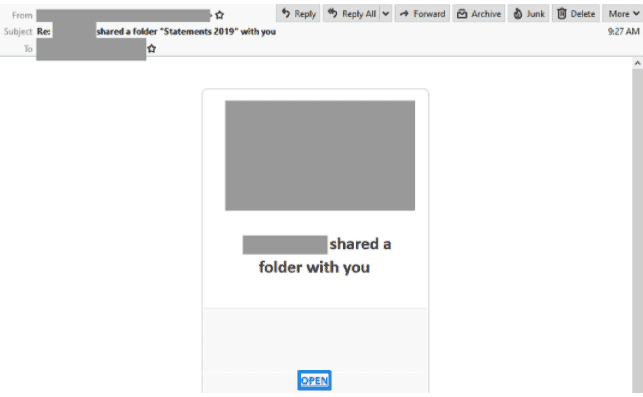
Shared Folder Phishing Email
- Appears as an automated message to ‘share a new folder’ with the title ‘statements 2019’.
- Includes a link to open the folder with the logo of the company it purports to be from and ends with the signature and contact details of an office manager.
- Originates from a freemail address given by Microsoft’s Outlook service.
- Clicking the link to open the folder leads to a intermediary site which requests the users click a download link.
- The page contains details of the “folder” including name and size.
- Users are requested to login with the email service they prefer.
- Once the users submits these credentials, the page redirects to another page, convincing them the login was successful.
- The only external reference is in the login form, which is where the login details are sent. This is likely an evasion tactic to reduce the risk of external links being intercepted by email security filters.
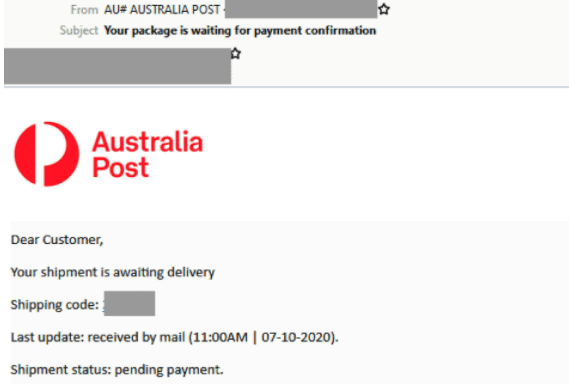
Australia Post Phishing Email
- Claims to be a notification from Australia Post.
- Sent by a specially created scam domain, it is titled “Your package is waiting for payment confirmation” and uses the display name “AU# AUSTRALIA POST”.
- Informs users that their “shipment is awaiting delivery” and requests payment confirmation via the link provided.
- Hovering over the words within the copyright line, shows the use of a shortened link which is used to hide the true link destination.
- Unsuspecting recipients who click on the link are led to a fake Australia Post-branded page requesting their credit card details.
- Australia Post’s logo and branding are used, however the domain used (‘australiainfoo.com’) doesn’t belong to the postal company and is hosted on a compromised WordPress page.
- Once recipients submit their payment details, it leads users to another page prompting them to submit an SMS code.
- “#AU” within the display name – this should raise the users suspicion about the email’s legitimacy.
- If you suspect that you have received a scam email pretending to be from Australia Post, please forward it to scams@auspost.com.au
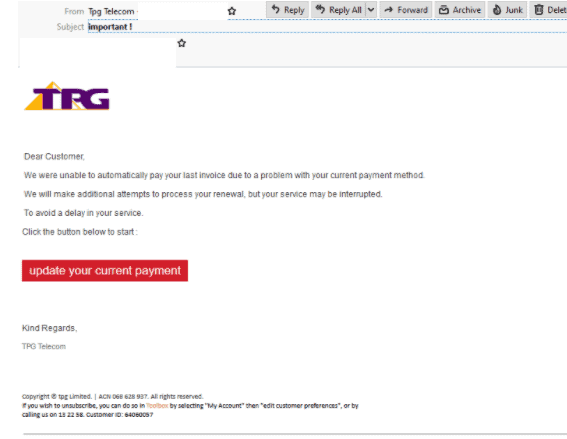
TPG Phishing Email
- Claiming to be from telecommunications giant TPG, it is titled ‘“important!” and employs the display name “Tpg Telecom” with the company’s branding and logo.
- A parody of a TPG support account has been used as the sender but it actually originates from a third party service called register.com.
- Informs users of a “problem” with their “current payment method” and advises they update their payment details via a provided link or risk “a delay” in their service.
- Ending with a TPG footer, hovering over the details reveals a shortened link which hides the true link destination.
- Recipients who click on the link to update their payment details are led to a convincing copy of a TPG login page.
- A compromised website hosted in Europe has been used instead of a TPG owned domain.
- There is also a stray PHP tag (“?>”) towards the bottom of the page.
- The phishing page is designed to steal user details which leads to another page requesting credit card information upon submission.
- Once credit card details are input, the page redirects to a verification code request which never arrives.
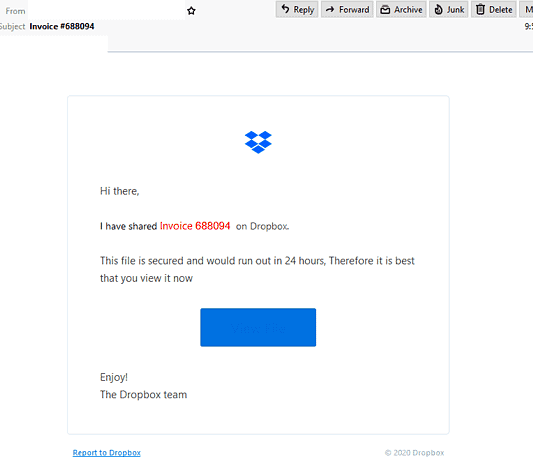
Dropbox Phishing Email
- Claiming to be from Dropbox, this scam informs recipients that someone is sharing an invoice with them “on Dropbox”.
- Urges users to “view it now” as the file “would run out in 24 hours” which is a ploy to make users panic and open the file without checking it’s legitimacy.
- The display name and email address used don’t belong to a Dropbox owned domain.
- Includes a button to view the invoice and the email ends with a sign-off from “The Dropbox” team.
- A shortened link has been used which hides the true link destination which is visible when hovering over the button.
- Recipients who click on the link to view the invoice are led to a fake Microsoft 365 login page asking them to verify their account which is hosted on a compromised website.
- Once recipients enter their details they are met with an error saying that the credentials are invalid.
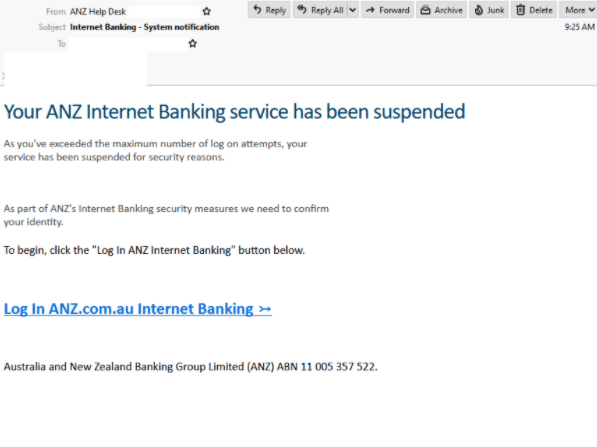
ANZ Phishing Email
- Titled “Internet Banking – System notification” and uses the display name “ANZ Help Desk”.
- Informs users that their Internet Banking service was suspended for security reasons and requests identity confirmation as part of the bank’s “security measures”
- Clicking the provided link leads recipients to a fake ANZ login page hosted on a GoDaddy phishing page and requests the Customer Registration Number and password.
- Upon submission of credentials, the page then asks for further security questions to be answered.
- Users are then met with an error requesting more security questions answers which are different to the ones previously provided. This occurs three times, a success message appears, and redirects to the real ANZ website.
- The aim of this scam is to obtain personal details which could lead to identity theft or accounts being accessed.
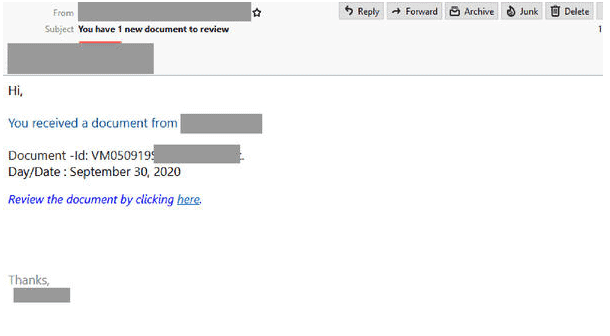
‘Review Document’ Phishing Email
- Titled “You have 1 new document to review” and sent from a compromised account.
- Display a document ID to boost credibility, it invites users to review by clicking on the provided link.
- Recipients who click on the link are led to to a fake Microsoft-brand login page hosted by Typeform, a popular website that specializes in online surveys.
- The subject reads: “Microsoft Office 365 Message Center”.
- Once the user submits credentials it redirects to a PDF document.
- A red flag within this scam is that when the password is entered, it is shown in its entirety which most authentic login pages wouldn’t allow for security reasons.
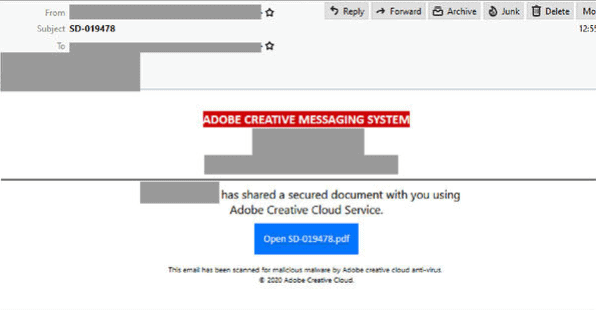
Adobe Creative Cloud Service Phishing email
- Masquerades as an automated file-sharing notification and originates from a compromised email address.
- With the title “SD-019478”, the email address within the “to:” field is the same as the sender’s email address.
- The header of the email uses the title “Adobe Creative Messaging System” and informs recipients that someone is sharing a “secure document” “using Adobe Creative Cloud Service”.
- The footer states “this email was scanned for malicious malware by Adobe creative cloud anti-virus”.
- Those who click on the provided link are directed to a GetAccept branded page which is a sales enablement platform; however the domain used doesn’t belong to GetAccept.
- Includes a blurry file preview, and links to download or view the file which when clicked, redirects to another page requesting email account selection.
- Mentions Sharepoint, OneDrive and Office 365, but only uses logos and no modern branding.
- Once the email account is selected, users are redirected to another page which requests email address and password which upon entering leads to an invalid credentials error.
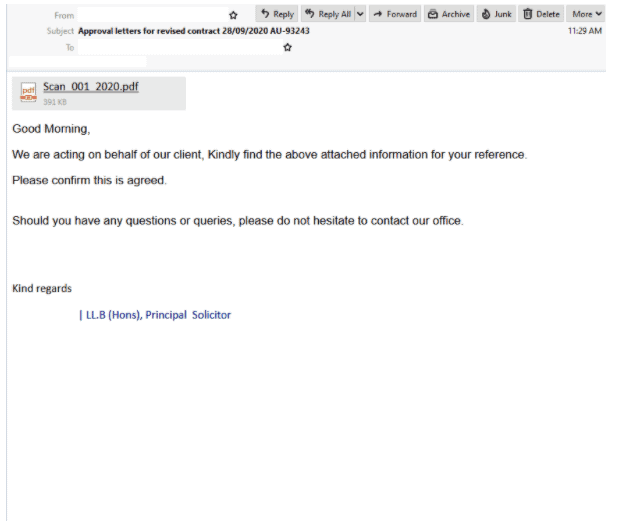
“Principal Solicitor” Phishing Email
- Masquerades as a notification from a “Principal Solicitor” at “Troylab Property Lawyers” with the subject: “Approval letters for revised contract”
- This organization doesn’t actually exist and the email has been sent from a compromised mailbox of another company.
- The email body includes an image of a .PDF file at the top, made to look like an attachment which is an external page link.
- Claiming to be “acting on behalf of” a client, it invites the recipient to view the above attach information and confirm the agreement.
- Redirected to a Google reCAPTCHA upon clicking the link, users are requested to confirm that they are not a robot – a feature used to evade detection on email security filters.
- Recipients who pass the reCAPTCHA are led to a fake Microsoft page which requests a username and password.
- An error message saying they were unable to login then appears once credentials are entered.
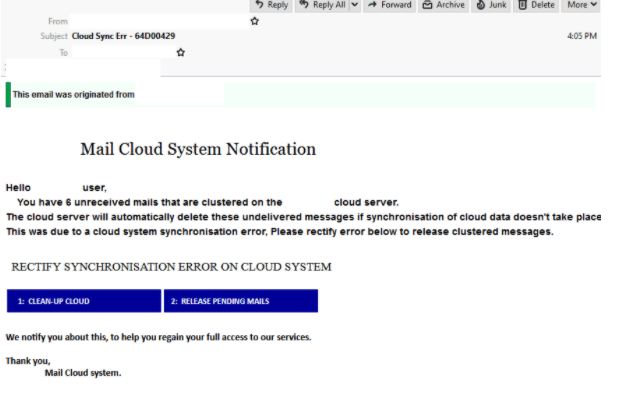
“Cloud Sync Err” Phishing Email
- Claims to be an automatic notification from recipient’s “Mail Cloud system”.
- Titled “Cloud Sync Err”, the email uses a display name indicating it is from the “cloud system”; however users a completed different domain which appears to be a German freemail address.
- In attempt to boost credibility, the header of the email states it originates from an internal source.
- It informs users that “due to a cloud system synchronisation error”, they have “6 unreceived mails ” on the “cloud server” which will be deleted if they don’t rectify the error by using the provided link.
- By clicking on the link to release these messages, it leads users to a fake Microsoft Outlook-branded page where login details are requested.
- This page then hosts a redirect script which was an official website for a former NFL footballer prior to it’s use as a phishing page hosted in Greece.
- Once the user submits their credentials they receive an error message that they were unable to login.
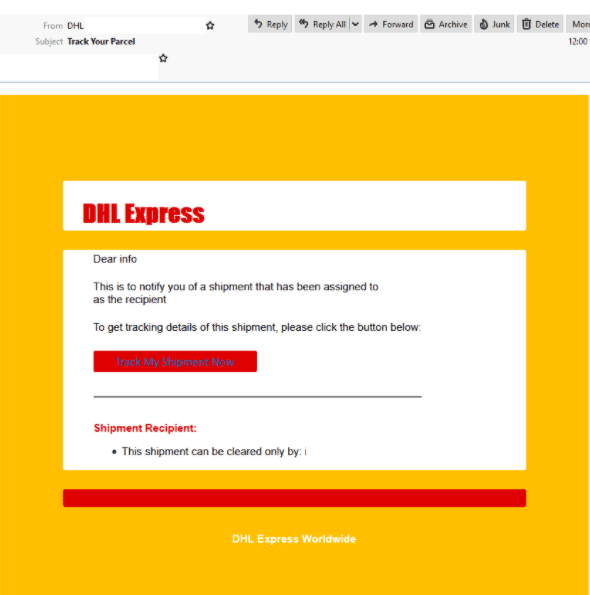
“DHL shipment” Phishing email
- A malicious email is purporting to be from DHL which comes from a compromised website of another US-based company.
- Titled ‘Track Your Parcel”, it informs recipients of a shipment coming their way.
- Those who click on the link to “track” the shipment are led to a fake DHL-branded login page requesting the user’s email address and password.
- The domain hosting the page doesn’t belong to DHL.
- Cybercriminals are preying on DHL customers who may think a ‘shipment’ is actually on its way. This motivates them to enter their personal details without hesitating.
- DHL emails should not be opened if:
- You have received an email without a tracking number and you are not doing business with DHL
- The email has an attachment and you are not aware that you are doing business with DHL
- The email instructs you to open an attachment for the tracking number
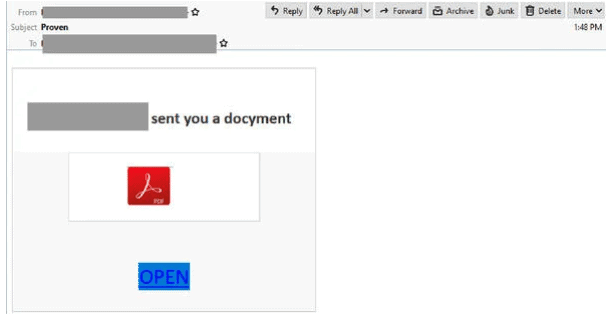
Adobe PDF “Docyment” Phishing email
- A compromised account is sending malicious emails which informs recipients that they have received a “docyment” in the form of an Adobe PDF.
- By spelling ‘document’ incorrectly, the attacker is aiming to circumvent email security filter rules.
- Clicking the link to “review document” leads recipients to an intermediary site requesting they click a download link which the directs recipients to a Microsoft Logo and OneDrive branded page.
- The page’s domain doesn’t belong to Microsoft and advised users must insert their email “to open this secure link”.
- Once users submit their email address, it requests their password which then leads to a message advising of an incorrect password.
If you’d like any further information, or assistance with your cyber security strategy or you don’t know where to start, please call us on 1300 478 738 or Email us.




