Surety IT provides a monthly security alert of the scams impacting Australian businesses including phishing scams, malware attacks and security breaches/bugs.
Most scams aim to harvest credentials, however there are many common red flags to look out for which include:
- Recipient not being directly addressed
- Sender domains don’t belong to the sites they claim to be from
- Branding not displayed correctly
- Spelling Errors
- Spacing and formatting errors
- Domains aren’t familiar or not legitimate
- Poor English used
- Omit personal details that a legitimate sender would include
- Sent from businesses that you were not expecting to hear from
- Stray PHP tag (“?>”) at the bottom of the email.
You need to be particularly aware of:
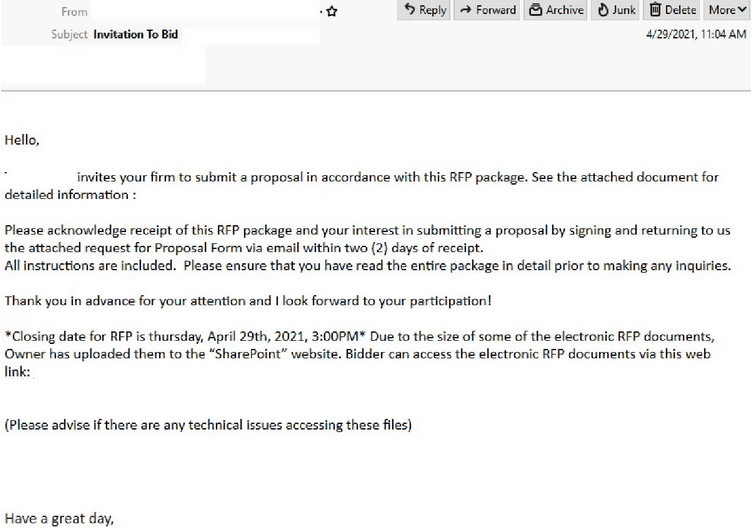
Microsoft & Adobe Spark Phishing Email
- With the subject of ‘Invitation to Bid’, this phishing email ‘invites your firm to submit a proposal in accordance with this RFP Package’.
- Due to the size, the file has been uploaded to SharePoint and a link is provided for recipients to view the documents.
- Originates from a compromised email account.
- Those who click on the link are led to a web page which requests another link be clicked in order to ‘view proposal’ which also includes the Adobe Spark logo and branding.
- Once the second link is clicked, users are prompted to sign in via a fake page purporting to be Microsoft which is actually a phishing page hosted on Cloudfare.
- If credentials are entered, these are then harvested by cybercriminals and prompted that the email or password is incorrect.
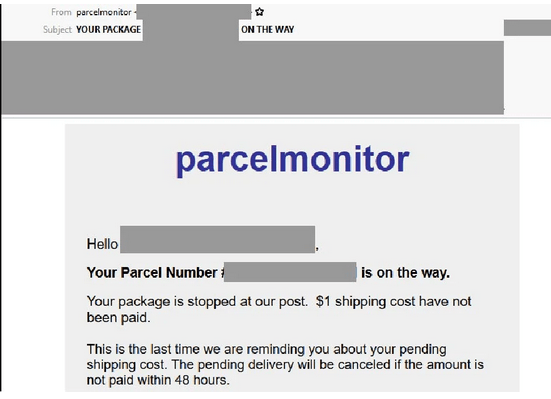
Australia Post Phishing Email
- Uses a Australia Post branding and a display name of ‘parcelmonitor’ and is sent using a compromised domain that doesn’t belong to parcelmonitor.
- The email reminds recipients to pay their ‘pending shipping cost’, adding that the delivery will be cancelled if not paid within 48 hours.
- Recipients who click on the provided link to ‘schedule their delivery’ are led to several phishing pages requesting user deliver preferences including time and shipping address.
- Domains used don’t belong to Australia Post.
- Once preferred delivery options are selected, users are then asked to provide personal details such as name, email, phone number and a password of their choice and also valid credit card details.
DHL Phishing Email 1
- Domain used in the senders email address has spoofed DHL and originates from a hosting provider based overseas.
- High quality DHL branding is used throughout including the logo.
- Informs recipients that ‘delivery attempt failed’ and warns that if it isn’t rescheduled or picked up within 72 hours, it will be returned to the sender.
- Those who open the HTML attachment are led to a phishing pages using Adobe PDF branding to log in.
- Once credentials are entered, recipients are redirected to a compromised external website hosted on Namecheap where information is harvested.
- Users are then redirected again to a domain associated with the users email address, for example, if Gmail is used, they are redirected to Google.

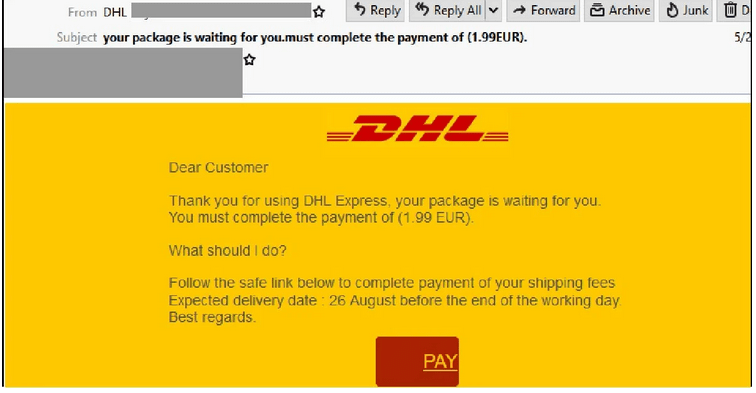
DHL Phishing Email 2
- Uses a display name of ‘DHL’ and uses the company’s branding.
- Senders email originates from a SendGrid account that is likely compromised.
- Informs users to complete payment of their shipping fee in order to receive the delivery.
- A tracking code, expected delivery date and a link is provided.
- Those who click ‘Pay’ are led to a phishing ‘DHL Tracking’ page and requested to confirm payment within 14 days by clicking the ‘next’ button.
- Users are then requested to provide credit card information, names, addresses and a verification code.
- The phishing pages used in this scam do not belong to DHL and are hosted on a third-party platform designed to harvest person details.